The Importance of Vulnerability Management
In today’s world, managing vulnerabilities is crucial. As cyber threats continue to rise in
frequency and complexity, organizations need to address vulnerabilities in their IT systems. Neglecting this responsibility can lead to data breaches, financial harm and lasting damage to reputation. Research studies show that companies with vulnerability management tend to experience less severe breaches compared to those without such programs. For instance, a study by CSO Online emphasizes the importance of vulnerability management, highlighting the advantage it provides in defending against cyber-attacks.
Key Steps in Developing a Vulnerability Management Program
Asset Identification
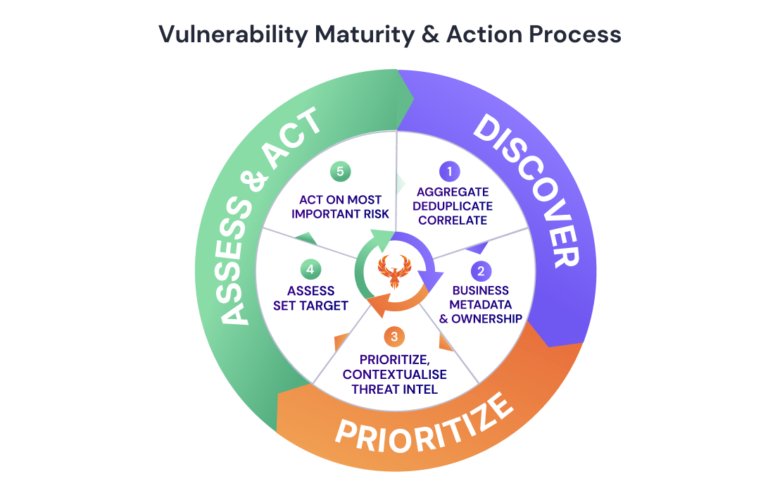
Building a vulnerability management program starts with asset identification. Organizations must have an inventory of all hardware and software assets they own. This inventory forms the basis for vulnerability assessments ensuring that no part of the IT infrastructure goes unnoticed. With detailed asset records, organizations can prioritize their security efforts and resources effectively by focusing on high-value assets.
Vulnerability Assessment
After identifying assets, the next step involves conducting vulnerability assessments. Regular security assessments entail systematically scanning a company’s IT setup to pinpoint weaknesses and vulnerabilities. Cutting-edge vulnerability scanning tools can generate reports highlighting vulnerabilities and suggesting ways to address them. Conducting these assessments regularly is crucial to staying ahead of emerging threats and ensuring that discovered vulnerabilities are promptly resolved.
Risk Prioritization
Not all vulnerabilities carry the level of risk. Hence it’s important to prioritize them based on their impact. The likelihood of exploitation. This step involves assessing the severity of each vulnerability, its associated risks, and the importance of the assets at risk. By aligning efforts to fix vulnerabilities with risk prioritization, organizations can concentrate on dealing with the severe vulnerabilities first, thereby enhancing their security
posture.
Remediation
Once vulnerabilities have been identified and ranked in terms of importance, remediation efforts can commence. Remediation entails taking measures to address the identified vulnerabilities. This could involve applying security patches, adjusting system configurations, or implementing security controls. Effective remediation is a process that necessitates collaboration among teams within the organization in areas such as IT, security, and operations. Formulating a clear and actionable remediation plan is essential for successful vulnerability management.
Monitoring and Reporting
Vulnerability management isn’t a one-off task but an ongoing endeavor. It’s important to check the IT system to find weaknesses and ensure that old ones don’t come back. Keeping everyone informed about how we’re managing vulnerabilities is crucial for transparency and responsibility. Giving stakeholders updates on how the program’s going helps us get the support and resources we need to keep things secure.
Automation in Vulnerability Management
In today’s world of vast IT environments, the use of automation has become essential for vulnerability management. Automation tools play a role in simplifying and improving aspects of managing vulnerabilities, such as conducting routine scans applying patches automatically and alerting promptly about newly identified vulnerabilities. By embracing automation, organizations can boost productivity. Reduce the time needed to address vulnerabilities. As an example, a recent article on Dark Reading pointed out that companies integrating automation into their cybersecurity plans can achieve more efficient vulnerability fixes, leading to a security foundation.
Real-World Examples
To demonstrate the benefits of vulnerability management, let’s look at how a financial institution has benefited from implementing an automated system. By searching for vulnerabilities and promptly applying patches, the institution prevented a data breach that could have jeopardized sensitive information belonging to thousands of customers. This proactive approach did not only protect the institution’s data. Also upheld customer trust and confidence.
Likewise a large retail chain saw improvements by updating and enhancing its vulnerability management practices. By checking for vulnerabilities addressing high-priority risks promptly and dealing with any petalia pagalworld identified flaws, the retail chain saw a 30% drop in security incidents year. This real-life example highlights how having a structured and ongoing system for managing vulnerabilities can help combat cyber threats and boost security within an organization.
To sum up, it’s crucial for companies to establish a vulnerability management program to safeguard their assets. By following a process that includes identifying assets, assessing vulnerabilities, prioritizing risks, taking action to fix issues, and continuously monitoring the situation, businesses can significantly lower their susceptibility to cyber threats. Moreover, using automation tools and top-notch industry resources can further improve the efficiency and effectiveness of vulnerability management efforts, ensuring a robust IT environment.